Implementing DMARC for Active Domains: Configuring Prerequisites
- Matt Zaske
- December 14, 2020
- 3 minutes
As a follow-up from my previous post about implementing DMARC controls for unused/alias domains (those not used for actively sending messages), I wanted to write a bit about how to implement basic DMARC controls for those domains actively used to send emails. What I'd started writing as an all-encompassing single post turned out to be kinda gnarly and too lengthy, so I have split this into two parts: this post (configuring DMARC prerequisites), and a follow-up post about crafting DMARC policy and review.
A Few Assumptions/Background
Most of my active/primary domains are managed through Google Workspace Admin, so these instructions assume you're using something similar. The reality, however, is that the basics are the same regardless of provider. These domains are used for sending email, so records should be deliberately tested and developed to avoid email delivery issues. Do NOT use (copy/paste) these examples on your own email domains unless you understand the values; doing so otherwise may very well ruin your day!
During the process of initial testing, I'd encourage you to use very low TTL values, at first in the 30 minutes or less category. When fiddling with DNS, very bad things can happen very quickly, and while it's usually easy to fix problems, the TTL values determine how long some areas of the Internet might be impacted.
As in the previous post, you'll want to be comfortable enough editing domain DNS entries, and I've added dig command examples to help you verify proper steps. If you're unfamiliar with any of the nomenclature or basics, please refer to that post. As a final bit of reference, I'm writing this from a clear Google Workspace angle; your provider(s) and senders may vary dramatically. What I've discovered is that good sending sources will help you (give you information) for your SPF and DKIM records.
1. Create/Update an SPF Record with all known origination points/sources
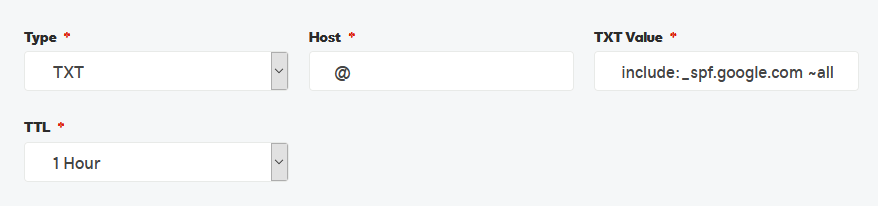
Google provides some great documentation on creating an SPF record, but the TL;DR: version is that you'll need to have (or add) this information in your DNS SPF Record:
v=spf1 include:_spf.google.com ~all
Pasting this information into your DNS record might look like this. Note that the TXT Value field isn't wide enough to show the entire string above, but it must be there!
DMARCLY has a quick guide with additional information about Google Workspace.
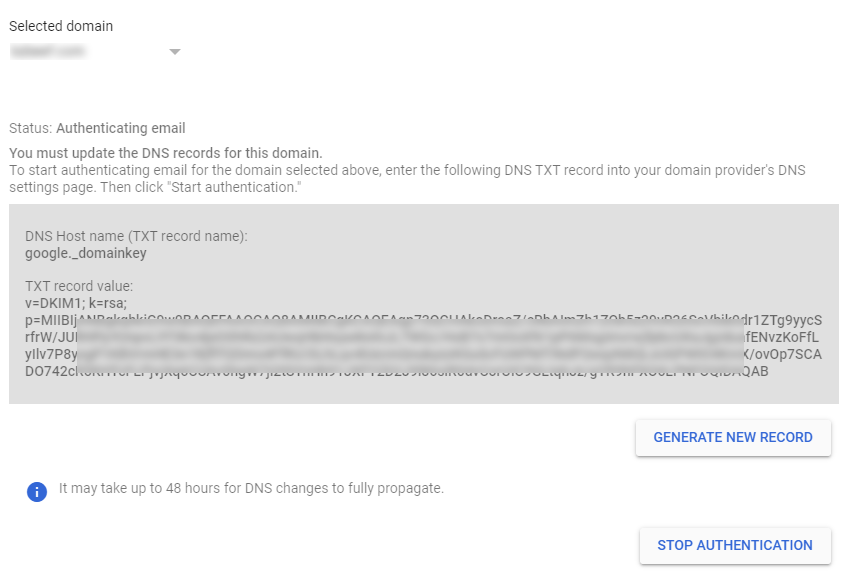
2. Create a DKIM Record for each origination point/source
Google also provides great documentation and a walkthrough to obtain a domain key for your DKIM record. The TL;DR: version is you'll have to add a record (provided) for your DNS DKIM Record, seen here as generated through Google Workspace Admin:
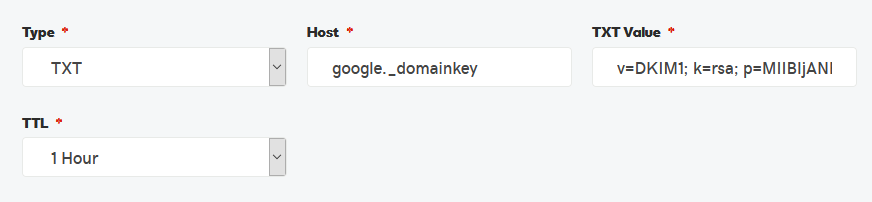
Entering that record into DNS would look like:
3. Test, Test, Test!
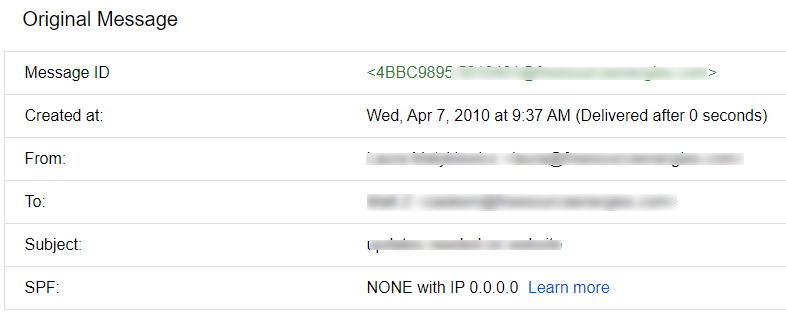
Ideally you'd let these settings do their thing for at least 48 hours, but in my own experience I had DKIM running for on the order of seven (or more) years for many email-sending domains and SPF in place for an extended period as well (~1-2 years) on one domain. That being said, there were a few where I bolted both in and let them sit for the better part of a week. During this time it's helpful to examine the headers ("show original" in Gmail) to see your progress. For example:
Before SPF and DKIM:
With DKIM, but without SPF:
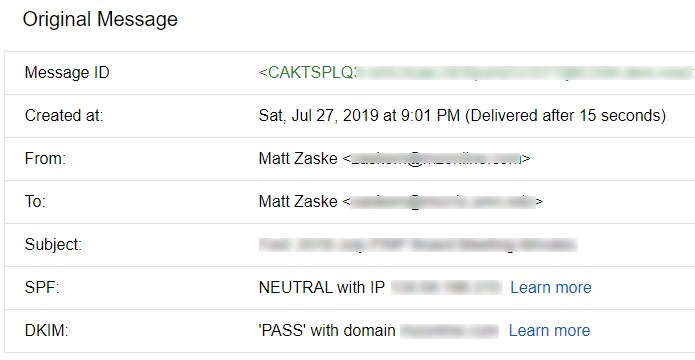
After SPF and DKIM:
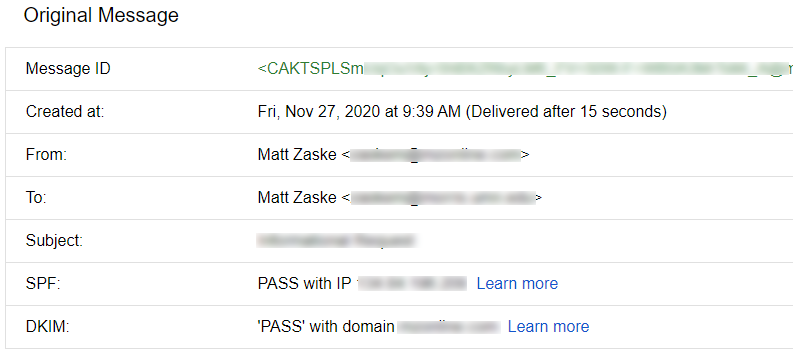
Once you've got messages being delivered (and ideally, 'PASS'ing both SPF and DKIM), you're ready to roll with a DMARC policy, which is covered in part two.






